Originally posted over on the Cube Soft Blog
As mentioned in our presentation at EngageUG – We came across a problem when adding multiple LDAP repositories in WebSphere.
The scenario was a Domino customer – who use the root domino domain – had a requirement for a second LDAP repository in connections to manage external users. They are a global company and via directory assistance grab the users that need access to connections but have no control over the records themselves. The plan was to have a 2nd domino domain for external users that the admins could manage independently of the main directory / domain.
We hit a problem as when using the domino root – it does all sorts of *fun* things inside WebSphere to overwrite any 2nd LDAP or additional base realm entries. After much testing with domino and ad as a 2nd LDAP, all the known work arounds didn’t resolve the issue, we opened a PMR.
As it turns out the answer was pretty simple:
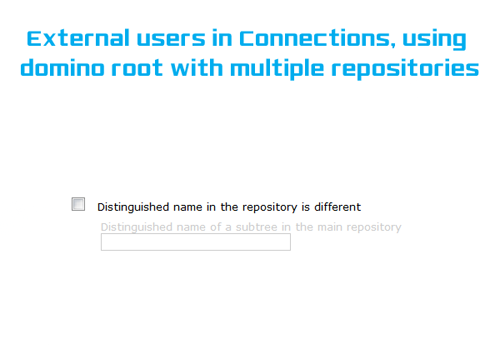
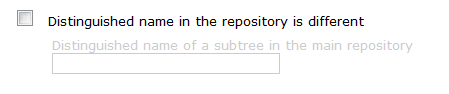
Set your domino root LDAP us as you would do normal – but, when you get to the point of adding the unique base entry to the realm add a name i.e o=dominoRoot (it doesn’t matter what this is as long as its o= something)
Select the tick the box to use a different distinguished name – leave the 2nd box blank
*EDIT* – you may need to add double quotes to provide a blank – i.e “” we will remove this in the next step
Save the config.
Next we need to edit the wimconfig to remove the offending entry that causes WebSphere to get confused.
The wimconfig can be found in <WAS_HOME>/profiles/Dmgr01/config/cells/<CELL_NAME>/wim/config
Find the entry relating to the new domino root entry .. and remove the duplicate base entry :
<wimconfig.xml>--------------------------------------------
<config:baseEntries name=""/>
<config:baseEntries name="o=dominoldap" nameInRepository=""/>
</wimconfig.xml>--------------------------------------------
remove the line
<config:baseEntries name=""/>
save and close the file and restart the deployment manager and connections nodes.
Once restarted the Domino root users and groups are still accessible inside WAS / Connections and it is now possible to add a second LDAP base entry correctly.
In the case of this particular customer we have added an External users AD, but another domino domain directory or any other supported LDAP should also work perfectly 🙂